-
Notifications
You must be signed in to change notification settings - Fork 18
Description
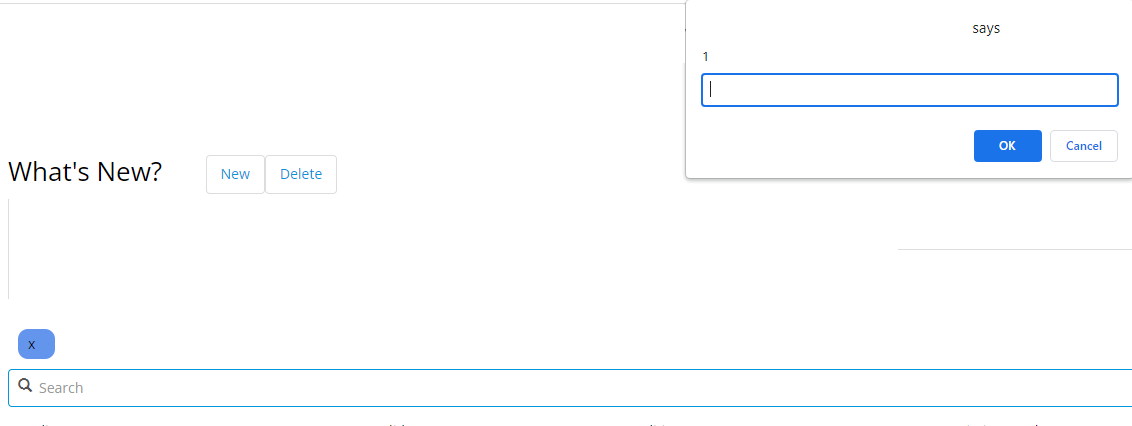
While conducting some security tests on my application, I noticed that I was able to perform Cross Site Scripting attacks through the Multifield search widget. With HTML as an example, users are able to insert and execute potentially malicious code by simply typing in the code snippet as a search query and hitting the Enter key.
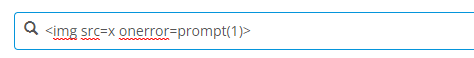
Attached are screenshots depicting a demonstration of this issue using an HTML image tag. The tag has an intentionally undefined source attribute, with the onerror attribute causing a prompt to appear in the web browser. Upon hitting the Enter key, the tag snippet was executed, and the prompt window appeared.
A potential solution could be something like implementing an event handler within the Multifield search, with the search string as an argument passed into a function that could utilize something like the "XSSSanitize" action from the Community Commons module. Alternatively, integrating code scrubbing within the Multifield widget could also be done, removing the need for the users to handle this security patch on their own terms.
The present concern is that at this time any hostile actor could go in and execute malicious code that could wreak havoc on applications, and while this could be handled on an app-by-app basis with custom remediation, this poses a risk to numerous Mendix applications that utilize this widget. Any solutions that could help remediate this issue would be greatly appreciated. Thank you!