The Simple FTP Honeypot Server is a lightweight low-interaction FTP service built with Python and Twisted. It is designed for defenders and researchers who want to safely observe FTP probing, brute-force attempts, and command patterns while collecting actionable logs for incident response and threat hunting.
- Low-Interaction Honeypot: Simulates an FTP control channel to capture attacker behavior without exposing a real filesystem.
- Configurable Banner: Set a custom
220welcome message via--banner. - Raw Bytes Telemetry: Logs raw inbound bytes (length + hex preview) in addition to parsed commands to help detect malformed payloads and potential zero-days.
- Better Protocol Fidelity: Handles common FTP commands (e.g.,
SYST,FEAT,TYPE,NOOP,HELP,QUIT) and returns realistic response codes. - Credential Capture: Records USER/PASS attempts and enforces a configurable attempt limit (default: 3).
- Clear Logging: Writes all activity to
ftp_honeypot.logfor later analysis.
- Python 3.x
- Twisted (
pip install twisted)
git clone https://github.com/0xNslabs/ftp-honeypot.git
cd ftp-honeypot
pip install twistedRun the server (defaults: 0.0.0.0:2121):
python3 ftp.py --host 0.0.0.0 --port 2121Set a custom banner (status code is enforced as 220):
python3 ftp.py --host 0.0.0.0 --port 2121 --banner "220 vsFTPd 3.0.3 ready"All interactions are recorded in ftp_honeypot.log. Logs include:
- New connections (client IP/port)
- Raw inbound byte telemetry (length + hex preview)
- Parsed FTP commands
- Captured credentials (USER/PASS attempts)
- Disconnect events
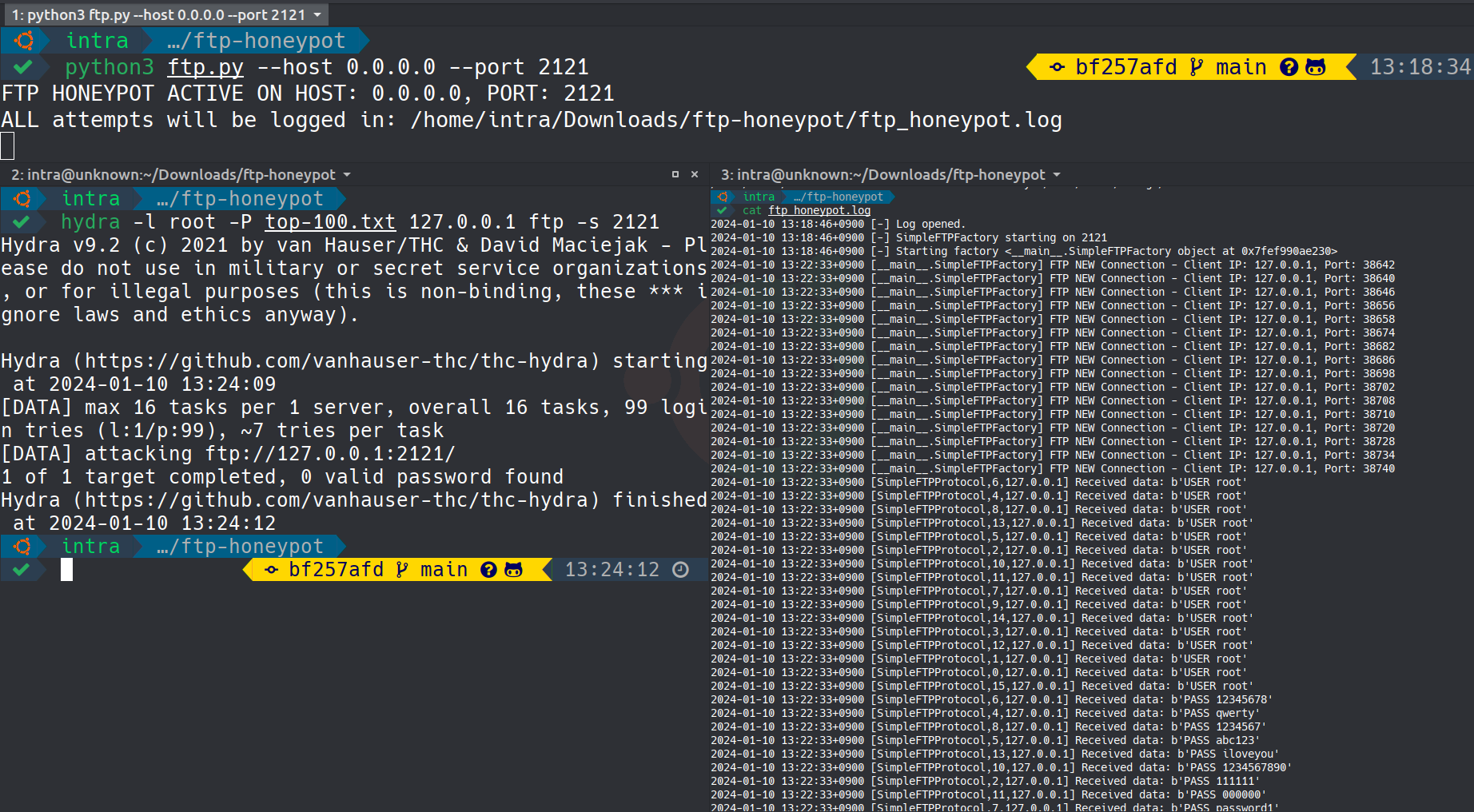 The above image showcases the Simple FTP Honeypot server capturing login attempts.
The above image showcases the Simple FTP Honeypot server capturing login attempts.
- DNS Honeypot - Monitors DNS interactions.
- FTP Honeypot - Simulates an FTP server.
- LDAP Honeypot - Mimics an LDAP server.
- HTTP Honeypot - Monitors HTTP interactions.
- HTTPS Honeypot - Monitors HTTPS interactions.
- MongoDB Honeypot - Simulates a MongoDB database server.
- NTP Honeypot - Monitors Network Time Protocol interactions.
- PostgreSQL Honeypot - Simulates a PostgreSQL database server.
- SIP Honeypot - Monitors SIP (Session Initiation Protocol) interactions.
- SSH Honeypot - Emulates an SSH server.
- TELNET Honeypot - Simulates a TELNET server.
- Caution: Deploy in a controlled environment (e.g., isolated VLAN, VM, or lab segment). Do not expose to sensitive internal networks without segmentation and monitoring.
- Compliance: Ensure compliance with all applicable local and international laws when deploying the honeypot.
This project is distributed under the MIT License. See LICENSE for more information.